
Specialised cybersecurity protection for industrial environments, legacy systems, and critical infrastructure.

Complete Cybersecurity Solutions. AI-Powered Threat Detection. Cloud-Ready, On-Demand, On Guard.
Specialist support and industry-best technology
Trusted by Defence. Trusted by Industry.
Logi-Tech delivers integrated technology and cybersecurity services tailored to enterprise and operational environments. Whether you're securing critical infrastructure, deploying new systems, or sourcing tech solutions, Logi-Tech ensures performance, protection, and peace of mind, powered by specialist support and industry-best technology. With nearly 40 years of experience bridging the gap between business and technology, Logi-Tech knows how to help you work smarter, faster, and more securely. When you partner with Logi-Tech, you get more than just tech support; you gain a local team that understands your business and stands behind your goals.

Next-generation cybersecurity
Future-Ready Security Solution for Operational Technology (OT) Networks
ARIA Zero Trust PROTECT (AZT PROTECT™) is a comprehensive AI driven defense system that protects all your OT endpoints from ALL cybersecurity threats – known and unknown.
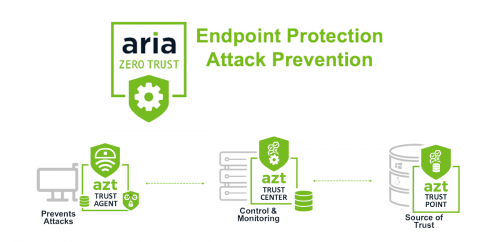
DETECT & DEFEND
Your New Security Operations Centre (SOC)
Companies across Australia that operate critical infrastructure must ensure they can respond to the rising threat of cybercrime and comply with new regulations and insurance expectations. For many businesses it is not economically or logistically feasible to create an in-house SOC. Logi-Tech have partnered with ARIA to provide a monitored, turn-key solution so that you can focus on what you do best.
Understand your risk profile with continuous testing
Network security validation in-depth
Map your internal attack surface | Challenge your internal controls | Prioritize exposure remediation
Focus on uncovering and addressing key vulnerabilities across your network through Automated Security Validation™. Thorough testing of every network segment identifies and rectifies vulnerabilities, misconfigurations, and exposed credentials promptly, preventing potential exploitation.
Embrace an attacker's mindset to rigorously test your security controls using a broad array of techniques from an extensive attack library, aligned with the MITRE ATT&CK® framework.
Prioritize and address the most critical vulnerabilities by understanding and mitigating the root causes of potential attacks. Continuous vigilance and enhancement of your security posture are essential in staying ahead of threats.